Facilities, Equipment, and Other Resources
Usability Dynamics, Inc. (UDX)
Enterprise Infrastructure & Technical Capabilities Documentation
Offices & Laboratories
UDX maintains physical headquarters in Durham, North Carolina, which serves as the company's legal domicile and provides conference facilities for client meetings, team coordination, and collaborative research activities. The facility includes dedicated workspace for technical staff and meeting rooms equipped with high-quality video conferencing systems for remote collaboration.
Founded in 2011 by two United States Marine Corps veterans from the 2nd Reconnaissance Battalion, UDX operates a distributed laboratory model where core development teams collaborate across secure networks. The company provides laptops, workstations, and specialized development environments for all research personnel. Technical and operational support is maintained by dedicated DevOps teams with experience managing enterprise-scale systems and classified operations support. All personnel maintain security clearance readiness and follow strict operational security protocols derived from defense contractor background.

Durham headquarters facility providing legal domicile and conference capabilities while demonstrating cloud-first operational model
The company's operational resilience was proven during Russia's 2022 invasion of Ukraine, when UDX's Kharkiv office was destroyed yet operations continued without interruption. This distributed approach demonstrates that modern research infrastructure transcends geographic boundaries through cloud-native architectures and redundant communication systems. Development teams are equipped with high-speed internet connectivity and backup communication systems to ensure uninterrupted collaboration. An appropriate communication channel and travel coordination plan will be established between project locations, with UDX prepared to host academic internships and provide mentoring support as needed.
Compute, Storage and Network Resources
UDX provides ephemeral, globally distributed infrastructure designed for cloud-hopping operations that treat all compute, storage, and networking resources as temporary and replaceable. The company processes over 30,000 deployments annually across multi-cloud architectures spanning AWS, Azure, and GCP platforms, with architectural contributions to systems processing over $50 billion in annual transaction volume with zero security incidents—demonstrating that truly global, provider-agnostic operations are achievable at enterprise scale.
The company's infrastructure approach centers on temporary, isolated environments that provide complete runtime traceability. Each environment automatically destroys itself after use while maintaining immutable audit logs—a revolutionary approach to eliminating technical debt and ensuring security consistency. This zero-persistence architecture ensures every deployment starts from a known-clean state with forensic-level audit trails.
Ephemeral Infrastructure: UDX's temporary isolated environments test, validate, and verify application changes with complete runtime traceability, destroying themselves automatically after use while maintaining immutable audit logs.
Their UDX Worker platform (GitHub repository) enables seamless transitions between cloud providers, regions, and runtime contexts through declarative YAML configurations, supporting over 30 programming languages with zero-downtime credential rotation. Storage and networking resources are abstracted through multi-cloud secret management detailed in their DevOps manual.
UDX has pioneered tactical edge deployment capabilities for disconnected and contested environments, including containerized deployments that operate in resource-constrained environments and autonomous systems that function without persistent connectivity. Their "Crypto Canary" methodology and Wright's Law mathematical modeling achieve measurable 1.38% cost reductions per deployment volume doubling. The company's structural security enforcement approach—where containers physically refuse execution unless all cryptographic conditions are verified—has been validated under extreme operational conditions, including systems that maintained operations during active military conflict.
Development Tools and Laboratory Equipment
UDX maintains specialized development and testing environments equivalent to university laboratory equipment. The company provides comprehensive development tools including the UDX CLI (AI-powered command interface), mCurl Intelligence (data extraction and analysis), and MySec Security (zero-trust secret management). All development personnel are equipped with high-performance workstations, specialized software licenses, and access to enterprise development environments supporting over 30 programming languages and quantum computing frameworks, as detailed in their decentralized DevOps architecture.
The company's development infrastructure features intelligent monitoring systems that catch problems before humans notice them—automatically rotating compromised credentials, detecting configuration drift, and enforcing policy compliance without interrupting developer workflow. This self-healing approach enables proactive governance throughout the software development lifecycle.

Proactive SDLC Governance: UDX's monitoring framework embeds real-time validation directly into software development lifecycle, enabling systems to auto-diagnose, validate secrets, detect drift, and enforce compliance.
The organization operates enterprise-scale DevOps infrastructure supporting over 1,500 repositories across GitHub and Bitbucket platforms, with automated testing and deployment capabilities. UDX has developed over 2,000 Infrastructure as Code scripts and manages 300+ automated cloud environments, providing the scalable testing infrastructure equivalent to university HPC clusters.
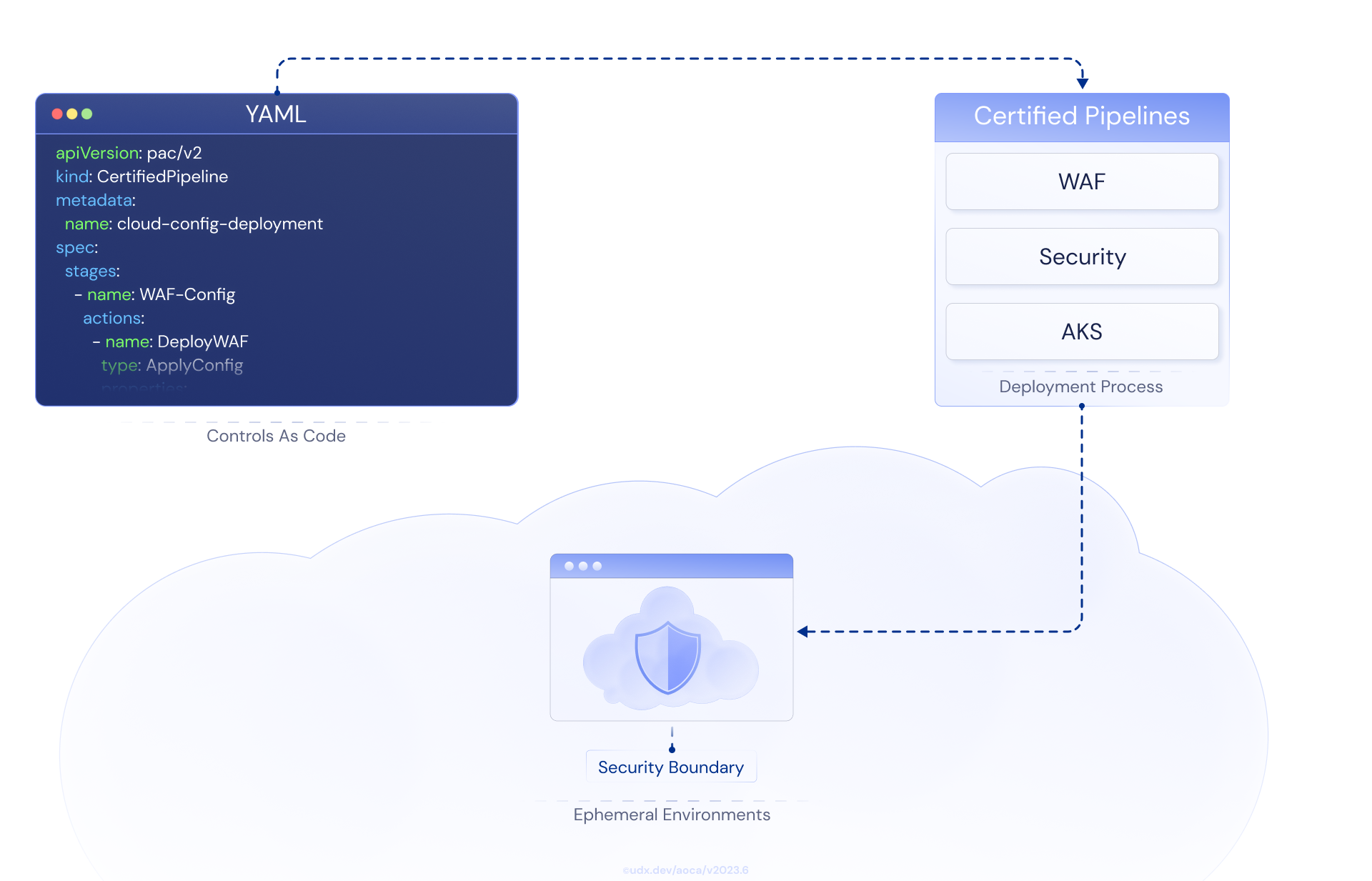
UDX's security-first approach makes insecure deployments physically impossible—containers literally cannot execute without cryptographic proof of compliance. Most companies bolt security onto existing pipelines; this architecture treats security as a structural prerequisite rather than an overlay, codifying security and compliance controls using declarative templates.

Security-First CI/CD: UDX's certified pipeline codifies security and compliance controls using declarative YAML templates, treating security as a structural prerequisite rather than an overlay.
UDX has contributed to the open-source community with over 1.3 million downloads of their software, including specialized data management and cloud integration tools. Their extensive GitHub organization showcases 33+ active repositories and enterprise solutions, demonstrating proven capability in collaborative software development and research reproducibility requirements.
Other Resources
UDX provides institutional collaboration capabilities through comprehensive technical documentation platforms and API development frameworks. The company successfully coordinated the Apple Pay Campus ID launch with Duke University—recognized by Apple as their "most successful partner launch ever"—demonstrating proven capability in academic-industry partnerships. Their Technical Documentation Platform supports automated generation of API documentation and integration examples, as demonstrated through their comprehensive DevOps manual.
The company maintains Software Supply Chain Security implementations that enforce organizational standards automatically—filtering packages through corporate policy constraints including valid licenses, compliant vendors, and security attestations before they reach production environments.

Supply Chain Security: UDX's software supply chain is hardened by structural controls, filtering packages through corporate policy constraints including valid licenses, compliant vendors, SBOM auditing, and threat intelligence before deployment.
UDX personnel maintain Security Clearance Ready status and follow strict operational security protocols derived from defense contractor experience. The company's distributed team coordination experience includes managing developers across multiple time zones and security clearance levels, with proven capability in USAID Cybersecurity Initiative and classified operations support.
Academic partnerships require open access for research transparency while enterprise contracts demand strict security. UDX's secure authentication architecture enables both requirements by creating authenticated environments with granular permission boundaries for controlled collaboration.
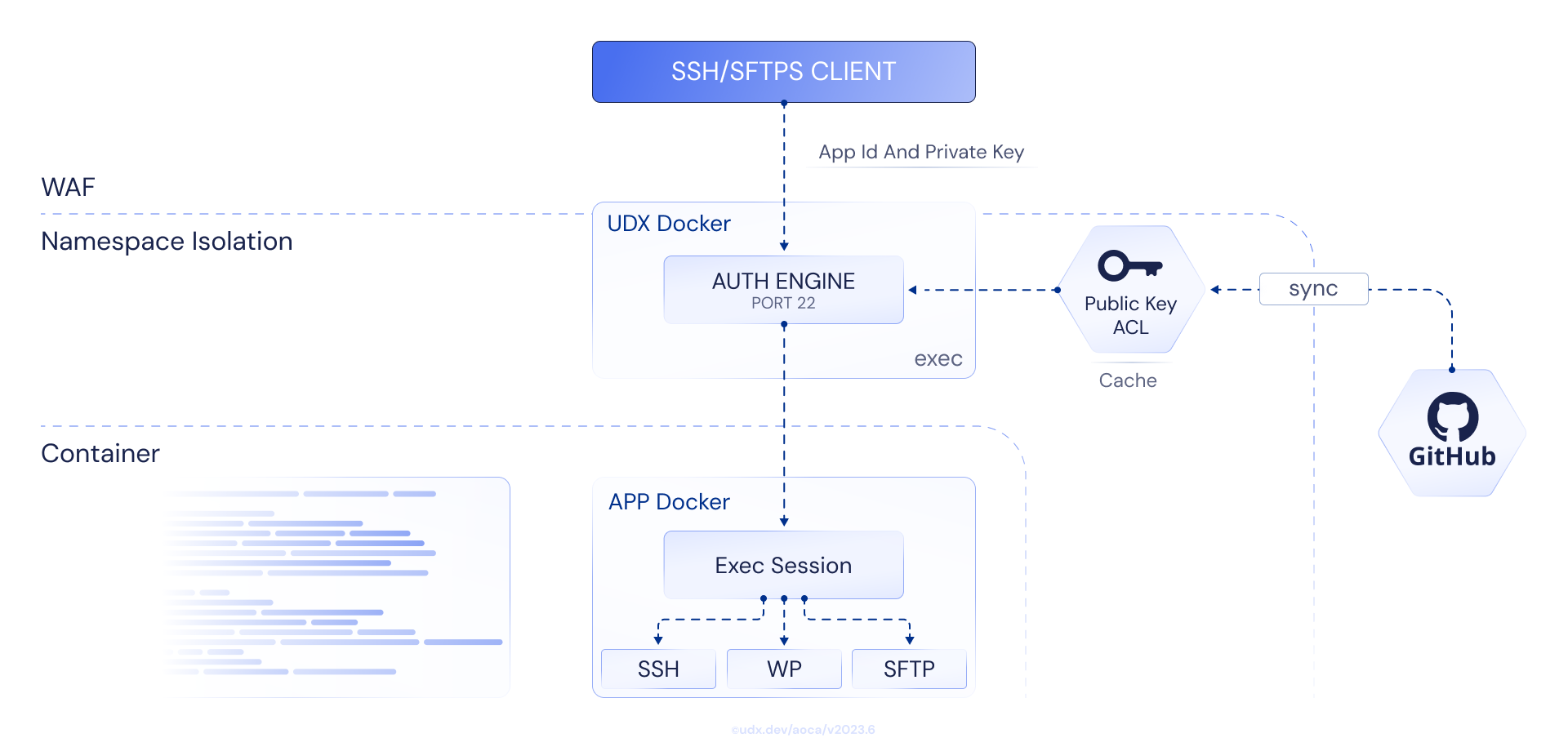
Academic Access Control: UDX's secure authentication architecture provides controlled access for academic collaboration while maintaining enterprise-grade security standards and compliance requirements.
UDX's Enterprise Payment Processing and Financial Services Pipeline experience demonstrates capability in handling mission-critical, high-reliability systems—with zero security incidents across $50+ billion in transaction processing. This financial sector experience is complemented by defense and intelligence work including cyber defense implementations and government-grade solutions requiring the highest security standards, as detailed in their operational track record.